Okara
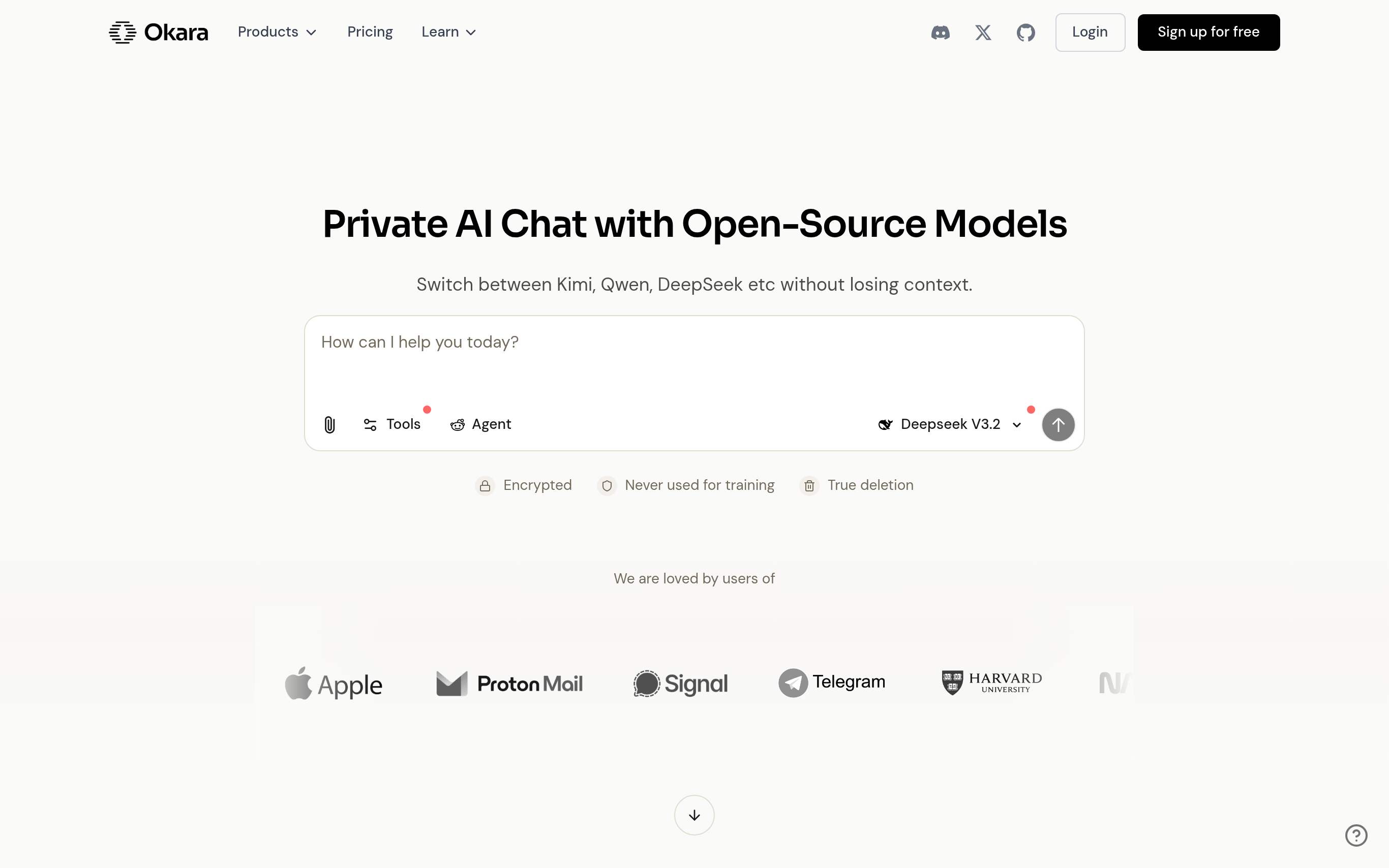
Okara is a private AI chat platform designed for professionals who prioritize both intelligence and data privacy. With access to over 20 open-source AI models like Qwen, DeepSeek, and Llama, users can seamlessly switch between models without losing conversation context. The platform ensures that user data is protected through end-to-end encryption and does not utilize interactions for AI training. This allows creators, researchers, and executives to generate insights and collaborate securely, free from third-party data harvesting. Okara is built not just to be compliant but to embody privacy as a core value of its architecture.
Basic Capabilities :
Unified Memory, End-to-End Encryption, Open-Source Model Access, Integrated Search Tools, Data Isolation
Basic Capabilities :
Unified Memory, End-to-End Encryption, Open-Source Model Access, Integrated Search Tools, Data Isolation
GOOD FOR
PERSONAL: Okara caters to individuals like writers, researchers, and students seeking private creative assistance and analytical support without compromising data. The platform ensures that all interactions remain confidential and offer enhanced functionalities.
BUSINESS: Designed for teams and startups, Okara streamlines workflows by providing a unified platform for collaborative work across multiple AI models. This leads to improved productivity and reduced risks of data breaches, making it ideal for professionals in sensitive fields.
BUSINESS: Designed for teams and startups, Okara streamlines workflows by providing a unified platform for collaborative work across multiple AI models. This leads to improved productivity and reduced risks of data breaches, making it ideal for professionals in sensitive fields.
FEATURES
Unified Memory: Users can switch between various AI models while retaining context, so all responses are informed by past interactions.
End-to-End Encryption: Conversations, prompts, and AI responses are encrypted both in transit and at rest, ensuring that user data remains confidential.
Open-Source Model Access: With 20+ models available, users can leverage the latest in AI technology without juggling multiple subscriptions.
Integrated Search Tools: Directly search web resources like Reddit, YouTube, and more, and incorporate live information into conversations for enhanced workflows.
Image Generation: Create professional-grade visuals using open-source image models, safeguarding sensitive creative briefs during the process.
Data Isolation: User data is never used for AI training or shared with third parties, maintaining complete control over personal information.
Team Workspaces: Enables collaborative work environments where teams can utilize shared AI capabilities securely and efficiently.
Client-Side Key Generation: The private encryption keys remain on user devices, ensuring that data is never exposed in plaintext.
Secure Upload Handling: Users can upload documents and media for analysis, which remain encrypted and are managed without exposure to external threats.
User-Controlled Decryption: Decryption of chat history is handled solely on the user’s device, putting control in their hands.
Rapid Deployment of New Models: New models are integrated swiftly into the platform, allowing users to stay up to date with cutting-edge technology.
Lifetime Access for Early Adopters: Founding users can secure lifetime access to the platform with a one-time commitment, reinforcing loyalty and continuity.
End-to-End Encryption: Conversations, prompts, and AI responses are encrypted both in transit and at rest, ensuring that user data remains confidential.
Open-Source Model Access: With 20+ models available, users can leverage the latest in AI technology without juggling multiple subscriptions.
Integrated Search Tools: Directly search web resources like Reddit, YouTube, and more, and incorporate live information into conversations for enhanced workflows.
Image Generation: Create professional-grade visuals using open-source image models, safeguarding sensitive creative briefs during the process.
Data Isolation: User data is never used for AI training or shared with third parties, maintaining complete control over personal information.
Team Workspaces: Enables collaborative work environments where teams can utilize shared AI capabilities securely and efficiently.
Client-Side Key Generation: The private encryption keys remain on user devices, ensuring that data is never exposed in plaintext.
Secure Upload Handling: Users can upload documents and media for analysis, which remain encrypted and are managed without exposure to external threats.
User-Controlled Decryption: Decryption of chat history is handled solely on the user’s device, putting control in their hands.
Rapid Deployment of New Models: New models are integrated swiftly into the platform, allowing users to stay up to date with cutting-edge technology.
Lifetime Access for Early Adopters: Founding users can secure lifetime access to the platform with a one-time commitment, reinforcing loyalty and continuity.
PRICING
FREE: Start with 5 credits, allowing for approximately 50 messages and access to all Pro features with limited usage.
INDIVIDUAL: For $10/month, users get 2,000 credits, enabling unlimited interactions with Lite models alongside standard features.
BUSINESS: For $15 per user/month, teams can access enhanced admin controls, SSO/SAML integration, and additional security features tailored for collaborative environments.
ENTERPRISE: Custom pricing available, with services tailored for large organizations, including enhanced security, compliance, and governance measures for high-stakes data handling.
INDIVIDUAL: For $10/month, users get 2,000 credits, enabling unlimited interactions with Lite models alongside standard features.
BUSINESS: For $15 per user/month, teams can access enhanced admin controls, SSO/SAML integration, and additional security features tailored for collaborative environments.
ENTERPRISE: Custom pricing available, with services tailored for large organizations, including enhanced security, compliance, and governance measures for high-stakes data handling.
TECHSTACK
AI Models – Utilizes the latest open-source AI models including Qwen, DeepSeek, and Llama, providing versatility for various tasks.
Encryption – Implements robust encryption methods for data in transit and at rest, ensuring complete user privacy.
Integration – Offers seamless integration with other tools and resources for comprehensive workflows, enhancing productivity.
User Authentication – Features client-side key generation for secure access control and encryption management.
Data Management – Employs user-controlled data processing, ensuring that only designated users can access or decrypt sensitive information.
Encryption – Implements robust encryption methods for data in transit and at rest, ensuring complete user privacy.
Integration – Offers seamless integration with other tools and resources for comprehensive workflows, enhancing productivity.
User Authentication – Features client-side key generation for secure access control and encryption management.
Data Management – Employs user-controlled data processing, ensuring that only designated users can access or decrypt sensitive information.
last update : January 21, 2026
