Worthify
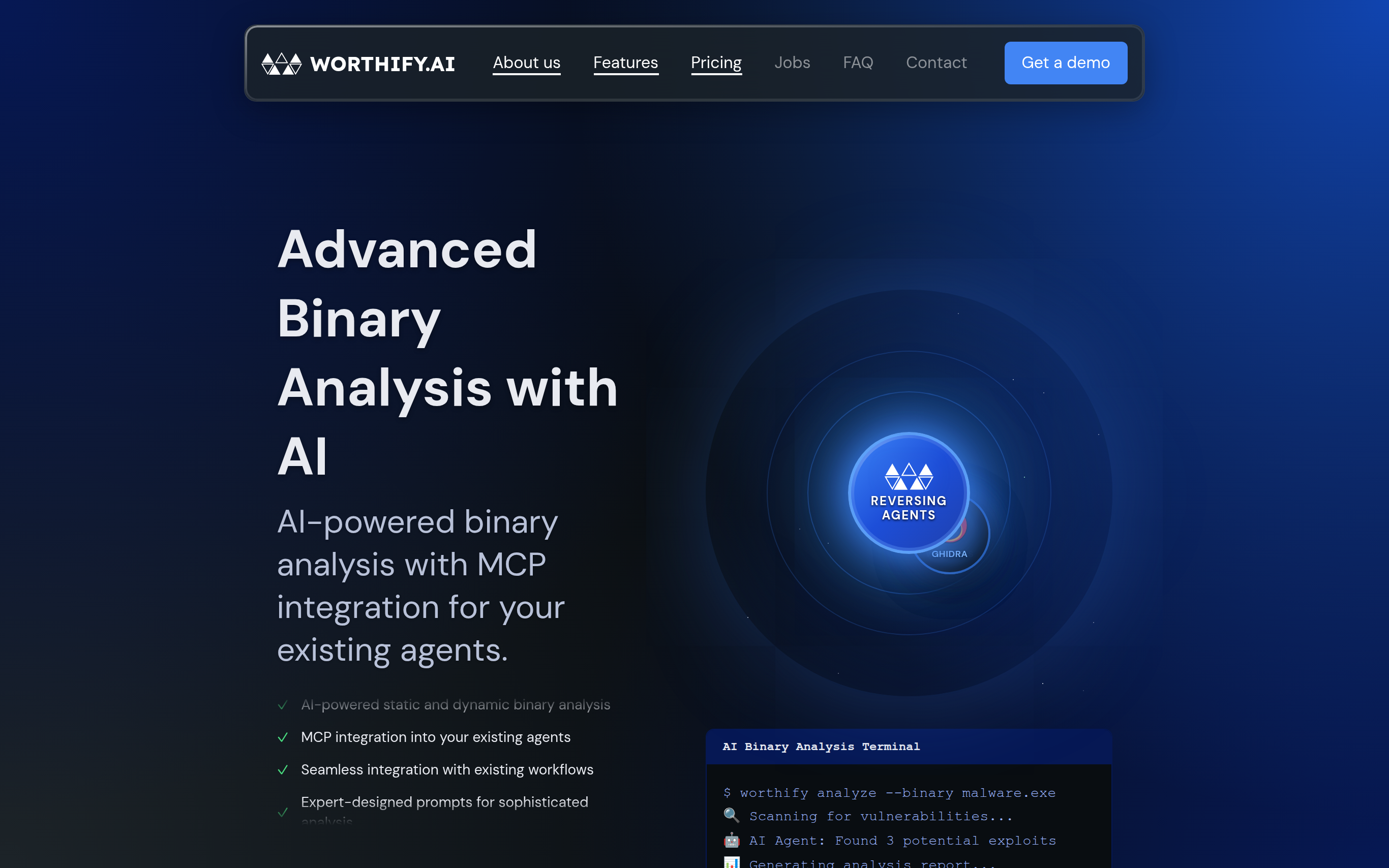
Worthify is an advanced AI-powered binary analysis tool designed to enhance the cybersecurity landscape through sophisticated deep analyses of executable files. It allows users to seamlessly upload binaries and interact with AI agents that provide insights on vulnerabilities, exploit recommendations, and comprehensive analysis reports. What sets Worthify apart is its ability to operate with maximum security in air-gapped environments while integrating with existing agentic systems via Model Context Protocol (MCP). Users can conduct inquiries on binary functionality and vulnerabilities using natural language, revolutionizing how analysts approach binary files and malware detection.
Basic Capabilities :
AI-Powered Analysis, Interactive Chat with Agents, Comprehensive Reports, Offline Analysis, Integration with MCP
Basic Capabilities :
AI-Powered Analysis, Interactive Chat with Agents, Comprehensive Reports, Offline Analysis, Integration with MCP
GOOD FOR
PERSONAL: Ideal for cybersecurity enthusiasts and independent researchers focused on malware detection, reverse engineering, and improving their technical skills with hands-on binary analysis.
BUSINESS: Targeted towards security teams, developers, and incident response professionals looking to optimize their workflows, enhance threat detection capabilities, and improve organizational security efforts through AI-powered tools.
BUSINESS: Targeted towards security teams, developers, and incident response professionals looking to optimize their workflows, enhance threat detection capabilities, and improve organizational security efforts through AI-powered tools.
FEATURES
AI-POWERED ANALYSIS: Instantly analyze binaries for vulnerabilities using advanced AI algorithms, providing timely insights necessary for effective cybersecurity measures.
INTERACTIVE CHAT WITH AGENTS: Users can engage in a dialogue with the binary through AI agents, asking specific questions to unveil vulnerabilities and code structures.
COMPREHENSIVE REPORTS: Generate detailed reports that include vulnerability assessments, exploit recommendations, and findings for improved security postures.
OFFLINE ANALYSIS: Perform in-depth analyses of binaries in secure, isolated environments, ensuring sensitive files are handled with maximal security protocols.
Integration with MCP: Seamlessly connect Worthify’s capabilities into existing security agent workflows using Model Context Protocol to leverage advanced analysis without disruption.
COMPATIBILITY WITH TOOLS: Integrates with popular analysis tools like Ghidra and offers compatibility with various VM environments for enhanced debugging and analysis processes.
Fuzzing CAPABILITIES: Conduct fuzz testing to find buffer overflow and memory corruption vulnerabilities, improving the robustness of binaries against potential threats.
CUSTOM AGENT INTEGRATIONS: Allows for tailored integration of AI capabilities with existing systems to enhance workflow efficiency and binary analysis tasks.
INTERACTIVE CHAT WITH AGENTS: Users can engage in a dialogue with the binary through AI agents, asking specific questions to unveil vulnerabilities and code structures.
COMPREHENSIVE REPORTS: Generate detailed reports that include vulnerability assessments, exploit recommendations, and findings for improved security postures.
OFFLINE ANALYSIS: Perform in-depth analyses of binaries in secure, isolated environments, ensuring sensitive files are handled with maximal security protocols.
Integration with MCP: Seamlessly connect Worthify’s capabilities into existing security agent workflows using Model Context Protocol to leverage advanced analysis without disruption.
COMPATIBILITY WITH TOOLS: Integrates with popular analysis tools like Ghidra and offers compatibility with various VM environments for enhanced debugging and analysis processes.
Fuzzing CAPABILITIES: Conduct fuzz testing to find buffer overflow and memory corruption vulnerabilities, improving the robustness of binaries against potential threats.
CUSTOM AGENT INTEGRATIONS: Allows for tailored integration of AI capabilities with existing systems to enhance workflow efficiency and binary analysis tasks.
PRICING
FREE: Basic access to binary analysis features, with limits on the number of files uploaded and analyses performed per month.
INDIVIDUAL: $29/month for personal users, unlocking expanded access to more comprehensive features and higher thresholds for analyses.
BUSINESS: $199/month per user, including SSO/SAML authentication, admin controls, and increased limits on binary uploads and processing capabilities.
ENTERPRISE: Custom solutions tailored to large organizations, encompassing enhanced security, compliance measures, governance features, and dedicated support for extensive binary analysis operations.
INDIVIDUAL: $29/month for personal users, unlocking expanded access to more comprehensive features and higher thresholds for analyses.
BUSINESS: $199/month per user, including SSO/SAML authentication, admin controls, and increased limits on binary uploads and processing capabilities.
ENTERPRISE: Custom solutions tailored to large organizations, encompassing enhanced security, compliance measures, governance features, and dedicated support for extensive binary analysis operations.
TECHSTACK
AI MODEL: High-performance local LLM for secure and efficient binary analysis.
RUNTIME ENVIRONMENT: Supports analysis in isolated VM environments to enhance security.
DATA INTEGRATIONS: Works with data from various security tools and frameworks for a comprehensive analysis suite.
APIs: Accessible API calls for analysis functions allow integration with existing agentic systems.
AUTH: Strong authentication protocols including SSO/SAML support for organizational users.
RUNTIME ENVIRONMENT: Supports analysis in isolated VM environments to enhance security.
DATA INTEGRATIONS: Works with data from various security tools and frameworks for a comprehensive analysis suite.
APIs: Accessible API calls for analysis functions allow integration with existing agentic systems.
AUTH: Strong authentication protocols including SSO/SAML support for organizational users.
last update : October 30, 2025
